Event Driven

Event driven programming is represented by the below flow chart:
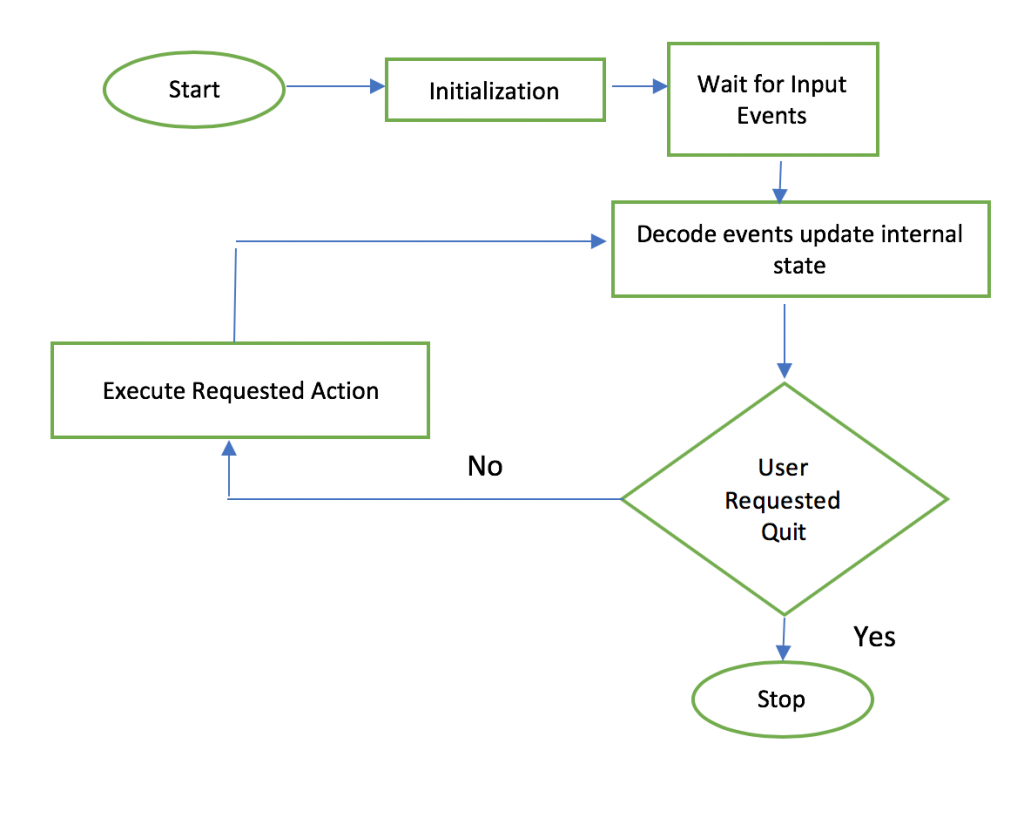 As I was looking at the flow chart above, I thought about how some people live event driven lives. What do I mean by this statement?
As I was looking at the flow chart above, I thought about how some people live event driven lives. What do I mean by this statement?
There are people who live in a state of rest and become initialized only when an event impacts their life. They may decide to act on the event, or they may decide to ignore the event and go back to their state of rest. If they choose to act, they decode the event, take action, and wait for the next event. There are some of us, who live from one event to the next, in an eternal loop, making decisions solely based on the input of events into our lives; basically letting circumstances run our life, instead of being proactive, which is how I prefer to live my life and to manage cyber security.
Event driven programming is very similar in that it receives input from a user and then acts according to the input. Most of our operating systems today, are event driven. A graphical user interface, GUI, is an example, which exists in most of the smart phones, tablets and laptop technology. When a user opens their device, they are able to click on many different icons, which can open an application, allowing them to complete the task that motivated them to initiate interaction with the device. We have a user that inputs an action, such as clicking, to then respond with another action, perhaps another click. This simplified example explains event driven programming.
Personally, I do not appreciate event driven programming, in that I find it to be limited; and the same is true for event driven cyber security programs.
For example, there is a cyber security incident, teams mitigate the incident, and then wait for the next breech, malware and/or sophisticated attack, against their enterprise to respond again. While this event driven model has been useful in the past, it cannot keep up with the abundance of events that are occurring today.
How do we change the event driven model? While it has been useful to make what has been complicated, simple, as we see with the adaption of technology in all age groups, it is nonetheless, important to be proactive. From a cyber security view, we need to get ahead of our adversaries.
How do we become proactive in cyber security? Cyber threat hunting can be preemptive against the bad actors. Cyber threat hunting helps security analyst search through multiple events and consume input from software that can help them understand the risk of the enterprise. Understanding risk is key to being proactive, and that actually makes sense. Risk is a driver in today’s cyber security assessment. If I am a security analyst, do I spend as much time on lab devices as I do with production devices that may have the “crown jewels”? No, and this is basically risk. The “crown jewels” would be assigned a high risk, which means as a security analyst, I am looking for suspicious behavior, spending more of my resources addressing high risk assets.
Reviewing an enterprise, that helps an analyst think like a bad actor, will help cyber security teams stop running from one event to another. Understanding risk can take a cyber security program to a proactive approach instead of event driven, the same came be said for our personal lives, be proactive. Do not let life circumstances take you to places you do not want to go – be Connected where you want to be Connected, not where someone else leads you.






