Securing the Internet of Things – IoT

A popular question for cybersecurity professionals is what keeps us up at night?
In the past, I often have found this to be a scare tactic, but lately I have been very concerned about securing IoT. Why?
As we retrieve real time data and count on this data as being accurate, it is important to know that the IoT devices are secure and transmitting data that has not been altered.
We are not ready to truly protect the Tsunami of devices that are presently online and transmitting data. This is what keeps me up at night; but it turns out that it does not have to.
I have a drive, even a mission to change the way we think about cybersecurity. It is a real shift in a traditional strategy which normally includes events and incidents which are displayed on one console. These incidents are built upon applications, identity and access manager, and data bases. I believe we need to move to a more agile strategy.
In order to help us address cyber security issues, arising from the wave of IoT devices inundating us with data, we need two capabilities. First we must have End Point Detection and Response and secondly, Augmented Intelligence, which can provide behavior analytics. Together these two elements provide a digital footprint to everywhere we travel on the internet.
When I first began working in cyber security, I repeatedly encountered Windows as the transition from IT into OT. Regardless of the industry, the source of their compromise would be Windows operating system, at level two; which represents the human machine interface into operational technology devices.
The solution we presented, while appearing elegant, would require a staff of highly qualified individuals to run it successfully. CISO’s wanted to be able to hire someone with minimum technical training who would intuitively be able to run the solution.
Today we have the ability to deliver what the CISO’s were looking for; with two capabilities covering eighty percent of IoT, with only twenty percent of the effort.
How is this possible? We are can offer advanced attack and insider threat detection to level two, it is very important to understand that the attack pattern by malicious adversaries is consistently the same.
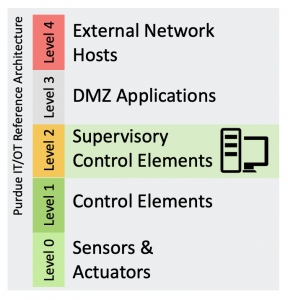
So what do I mean by that? If you look at the Purdue Enterprise Reference Architecture it shows you that beginning at level four, usually through phishing, which leads to reconnaissance, which leads to compromised accounts and machines, which lead to lateral movement, which leads to privileged escalation, which ultimately leads to a successful attack into critical infrastructure.
Today we can profile our IoT devices just like we can profile malicious adversaries as well as rough devices.
The fact is that for the first time in my career in cyber security, I do not have to be kept up at night. There is a way for all of us to stay safely Connected.






