The Anatomy of a Cybersecurity Attack

I have felt lately like we, in the cyber security community, are failing at our posts. Our clients are suffering from real day to day cybersecurity threats, turning off their computers at night, to wake up to the same scenario that they just left.
We keep saying if you do a little more, you will be okay, you are more secure. But then another data breach and they are back at square one, wondering what do they need to do, to be better.
I thought it might be interesting to understand the anatomy of a cybersecurity attack, because I had someone ask me about a VPN and what if they bought additional technology. While the attack below is on an industrial control system, the method of the attack is often the same.
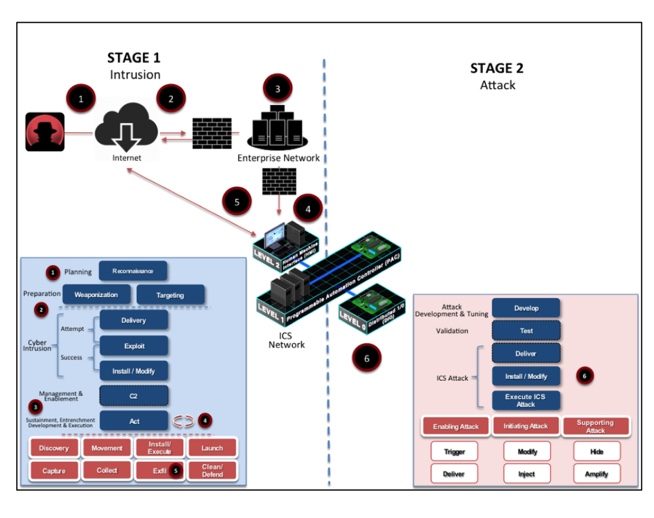
The first step shown as number 1 is the Planning and Preparation Stage, which lists Reconnaissance, Weaponization, and Targeting. Reconnaissance is about the bad actor selecting their Target, doing research and attempting to identify vulnerabilities. Weaponization is about the bad actor creating remote access malware, or buying remote access malware, which is readily available on the Internet, towards a discovered vulnerability.
The second step shown as number 2 lists the attempt and or success of the designer malware. If not successful the first time, it is not unusual for the attempt to be multiple times, in the thousands if not more. There are some tools that are able to pick up multiple attempts and the malware can be thwarted at this stage, but unfortunately, this does not happen often. But if the attempt is successful, then the bad actor now has their launching pad, a place where they may set up a backdoor to the system as an example.
The third step shown as number 3 is the command & control, known as C2, and the actually execution of the attack, will take place. This is an area where they may just observe and you will not even realize that the bad actor is in your system. It is not unusual for these attacks to have a dwell time of over a 100 days.
The fourth step shown as number 4 is the act. This is the area that the bad actor will use for data theft, ransomware or data destruction, and can just repeat their goal over and over again, until they are caught. As an example, data exfiltration may happen a little every night, this way they can remain under any thresholds that might be set in the cybersecurity tools.
The fifth step shown as number 5 are the actually use cases that have made the bad actor successful, and the sixth step, shown as number 6, takes the attack one step further in to the Industrial Control Systems, such as the electrical grid.






