Cognitive Security

Recently I was watching CNN: The Eighties; which had a show called; The Tech Boom. The show featured the digital revolution, including personal computers, very large cell phones, the space program, and the internet. It is almost hard to believe, where we started and where we are actually today. Everything grew so quickly, that computer security was an afterthought.
I often talk about the digital transformation when I speak to my clients. It was not long ago that firewalls and intrusion prevention devices were deemed as adequate to protect a business. But certainly today, the digital revolution has caused companies to require more security controls than one would have imagined. In fact, it is not unusual for a company to have eighty plus security products, from over forty-five different vendors. The technologies could include anti-virus, anti-malware, database, application and network firewalls, all products needing individual attention with critical vulnerabilities, usually maintained by five to ten employees.
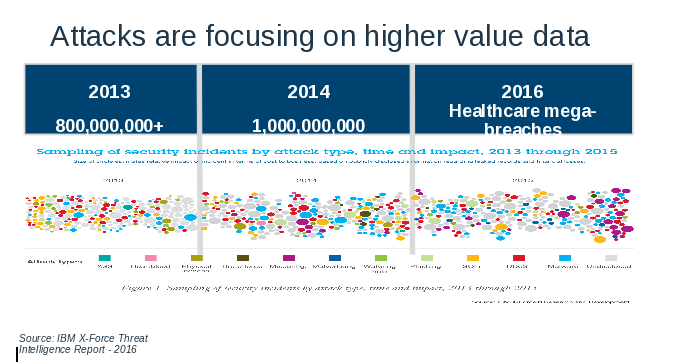
It is at this point in the conversation with my clients that I usually show the chart below:
The bubbles represent attack vectors which have grown exponentially from year to year, but notice the purple bubble at the end of the chart. The purple bubble represents the misconfigured device. A misconfiguration can represent something as simple as an Adobe patch that has not been applied. And it only takes one misconfigured device to take advantage of a business or individual, such as the case in ransomware.
Now how do we bring together, the technology boom and security? What steps do we need to take, so that we can take advantage of the opportunities that has been brought by the digital revolution?
Well today, I liken the security strategy found in many businesses to watching children play soccer. I do not know a lot about soccer, but we had spent time with Argentinians who had gone to see one of my colleagues children’s soccer game. The next day they endearingly referred to the game as swarm ball, because all the children would chase after the ball, not leaving any defense on the field. Today, we are like children chasing the bubbles, and leaving our digital field wide open.
When you look at all the bubbles, what can you do other than chase the latest critical vulnerability in your environment? This is why security needs to be revolutionized as well, thus today we move to cognitive security, or in IBM terms, Watson for Cybersecurity.
What is cognitive security and why is it needed?
The digital revolution produces 2.5 quintillion bytes of data every day. Quintillion represents 10 to the 18th power. Eighty percent of this data is unstructured, meaning it does not reside in a database, known as structured. Unstructured data can be represented by word documents, pictures, or videos, as an example. Basically, we understand natural language which can be considered, unstructured, and computers understand, structured.
Cognitive security is necessary, because we need a security tool to be able to analyze a threat like a human and understand the unstructured data that provides the intelligence to resolve the threat. Presently, there are thousands of security blogs with threat intelligence that help security analyst handle the latest breaches. But the process can literally take weeks to address, and in addition the average security analyst can receive up to twenty offences for a medium size business. Frankly this is why we see so many breeches of our data in the news. The process just takes too long.
Cognitive systems for cybersecurity is being built with the instincts and expertise of a security analyst that is able to analyze research reports, text, threat data, and other relevant unstructured and structured data, exponentially faster than a human, minimizing weeks to address a security event down to days.
While cognitive security is still in a learning stage, (Watson thought that ransomware was a city, and a back door was a back door to your house), it of course, a quick study, the result will diminish cybercrime, as the economics will not be worth the investment of time. Until this time, stay safely connected.